 Identify emerging technologies
Identify emerging technologies
List and explore the 10 most relevant Emerging Technologies for any topic relevant to you or your organization.
With our new generative-AI enabled, collaborative Emerging Technologies tool you and your colleagues can create an overview with a single mouse-click. Each of the 10 listed most relevant technologies can form the basis of a deep, but at the same time both efficient and explorative exploration and understanding of that particular technology.
As an example let's explore the 10 most relevant emerging technologies related to “cybersecurity for infrastructure”
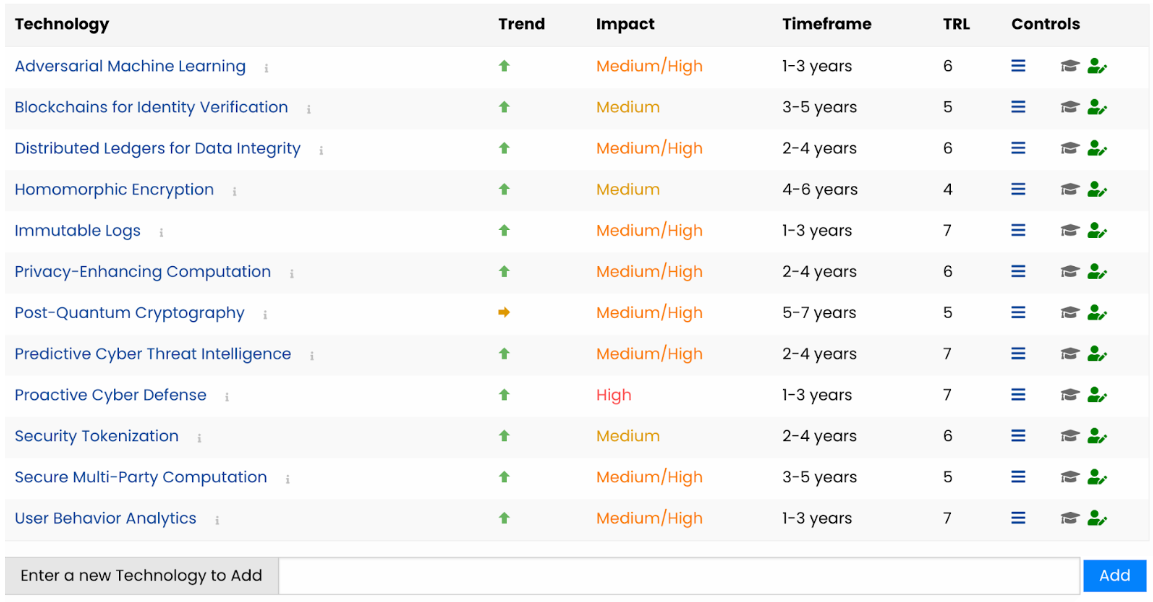
For each technology listed you get a indicator for:
Trend
Impact
Timeframe
TRL (Technology Readiness Level)
a set of controls
With the control depictured by ‘3 horizontal lines' for each listed emerging technology, you can with a single mouse click select and create any of the following rich expansions of that particular technology based on the present available intelligence from the continuous horizon scanning:
Business Case
Use Cases
Consequences
Implications
Policy Options
Now What?
Each of these selections will provide you with an overview as a ‘shallow dive' into your emerging technology of interest – All based on the very latest available intelligence from our continuous horizon scanning
|
1. User Behavior Analytics in Cybersecurity for the Infrastructure Sector User Behavior Analytics (UBA) is an essential tool in providing advanced security for critical infrastructure systems. These systems often serve as major targets for cyberthreats due to their essential contributions to the functioning of society, such as energy production, water supply, and transportation. Therefore, implementing a UBA system can significantly elevate their defence against potential threats. 2. Improving Threat Detection UBA effectively detects anomalous behavior by establishing a base normal behavior pattern for users and subsequently identifying deviations. This ability to pinpoint unusual activity allows early detection of potential threats, such as insider threats, targeted attacks, or compromised credentials. 3. Reducing False Positives By monitoring and learning user behavior, UBA can significantly reduce the rate of false-positive alerts, which often occurs with rule-based security systems. This specificity leads to more effective utilization of security resources for responding to genuine threats. 4. Enhancing Incident Response UBA provides detailed information about unusual user activities, such as the devices used, the location of logins, and the time of the occurrence. These data insights contribute towards a speedy and accurate investigation of security incidents. 5. Compliance and Regulation Complying with security regulations is a necessity for infrastructure systems. The data logged by UBA tools can serve as evidence for compliance audits by providing traceable and measurable records of user activities and incidents. 6. Improving Overall Security Posture By integrating UBA with other security technologies such as Security Information and Event Management (SIEM) and Data Loss Prevention (DLP), organizations can achieve a more comprehensive view of user behaviors and system security, enhancing their overall security posture. In conclusion, UBA plays a pivotal role in categorizing and mitigating cybersecurity risks in the infrastructure sector. By identifying and neutralizing threats early, reducing false positives, and aiding compliance efforts, UBA promotes a safer and more secure operational environment. |
|
Use Cases for Predictive Cyber Threat Intelligence in Infrastructure Sector 1. Threat Prevention and Detection Predictive Cyber Threat Intelligence can be used to predict possible threats before they occur. This helps infrastructure organizations to be proactive and prepare for possible attacks. The information can be used to detect threats in real time, helping to reduce the chances of success for cybercriminals. 2. Strategic Decision Making Intelligence derived from predictive cyber threat tools can be used to make strategic decisions. Leaders can prioritize risks depending on their potential impact and likelihood, allowing for optimized resource allocation. 3. Compliance with Cybersecurity Requirements Infrastructure organizations need to comply with a variety of cybersecurity regulations. Predictive Cyber Threat Intelligence can provide insights into potential vulnerabilities in their systems and help them ensure they meet all necessary compliance requirements. 4. Risk Analysis and Management Cyber threat intelligence can provide comprehensive insights into the potential threats. This can aid in risk analysis, helping organizations identify where they have vulnerabilities and how they could potentially be exploited, allowing for better risk management and mitigation strategies. 5. Incident Response In the event of a security breach, predictive intelligence can aid in determining the nature and extent of the breach. By understanding the potential threats, an effective response can be formulated swiftly, minimizing damage and downtime. |
And each trend listed you can click on and deeper investigate applying a whole range of additional foresight tools.
Should you not intuitively comprehend any of the technologies listed, click on the “i” after the name of each technology, this will provide you with the underlying reasoning why this particular technology is listed under your present scan.
You may not fully agree with or have other sources informing you differently on the value of any of the indicators - If you would like to alter any of the values listed you can easily do so using the Edit Control, which lets you edit any of the listed values. This may be important as each table is automatically saved for later use and reference.
We feel convinced that you will find our Emerging Technologies tables very powerful for your better understanding of what is to come and immensely time saving in your research and understanding of our futures.